- cnnvd编号:未知
- 危害等级: 高危

- cve编号:cve-2021-1675
- 漏洞类型: 未知
- 威胁类型:未知
- 厂 商:未知
- 漏洞来源:金山毒霸
- 发布时间:2021-07-01
- 更新时间:2021-07-01
漏洞简介
2021年6月8日,微软在6月份补丁日更新中通报并修复了windows print spooler远程代码执行漏洞(cve-2021-1675)。日前,该漏洞的poc已在网络上公开。
windows print spooler是windows的打印机后台处理程序,广泛的应用于各种内网中,攻击者可以在漏洞环境中绕过rpcaddprinterdriver的身份验证,并在打印服务器中安装恶意驱动程序。若攻击者所控制的用户在域中,则攻击者可以连接到dc中的spooler服务,并利用该漏洞在dc中安装恶意驱动程序,从而可能控制整个域环境。
该漏洞广泛存在于各个windows版本中,利用复杂度为中,但由于成功利用该漏洞的攻击者可以完整的控制域环境,攻击可能造成的后果严重,所以该漏洞的利用价值极高。
2021年6月29日,国外安全研究人员在github上公开了windows print spooler远程代码执行漏洞的poc。毒霸安全专家建议相关用户尽快升级系统以修复该漏洞,避免受到黑客攻击。
漏洞公示
参考网站
受影响实体
- windows server 2008 r2 for x64-based systems service pack 1
- windows server 2008 for x64-based systems service pack 2 (server coreinstallation)
- windows server 2008 for x64-based systems service pack 2
- windows server 2008 for 32-bit systems service pack 2 (server coreinstallation)
- windows server 2008 for 32-bit systems service pack 2
- windows rt 8.1
- windows server 2012 r2 (server core installation)
- windows server 2012 r2
- windows server 2012 (server core installation)
- windows server 2012
- windows server 2008 r2 for x64-based systems service pack 1 (server coreinstallation)
- windows 10 version 1909 for arm64-based systems
- windows 10 version 20h2 for arm64-based systems
- windows 10 version 20h2 for 32-bit systems
- windows 10 version 21h1 for 32-bit systems
- windows 10 version 20h2 for x64-based systems
- windows server, version 2004 (server core installation)
- windows 10 version 21h1 for arm64-based systems
- windows 10 version 21h1 for x64-based systems
- windows 8.1 for x64-based systems
- windows 8.1 for 32-bit systems
- windows 7 for x64-based systems service pack 1
- windows 7 for 32-bit systems service pack 1
- windows 10 version 2004 for x64-based systems
- windows 10 version 2004 for arm64-based systems
- windows 10 version 2004 for 32-bit systems
- windows server 2016 (server coreinstallation)
- windows server 2016
- windows 10 version 1607 for x64-based systems
- windows 10 version 1607 for 32-bit systems
- windows 10 for x64-based systems
- windows 10 for 32-bit systems
- windows server, version 20h2 (server core installation)
- windows 10 version 1909 for x64-based systems
- windows 10 version 1909 for 32-bit systems
- windows server 2019 (server coreinstallation)
- windows server 2019
- windows 10 version 1809 for arm64-based systems
- windows 10 version 1809 for x64-based systems
- windows 10 version 1809 for 32-bit systems
补丁
目前微软已修复该漏洞并发布了安全版本,毒霸安全团队强烈建议用户立即更新windows至最新版本。
若用户暂时无法进行补丁更新,可以通过禁用print spooler服务来缓解漏洞风险。
临时正规网赌十大娱乐棋牌的解决方案:
运行service.msc,在服务列表中找到printspooler服务。
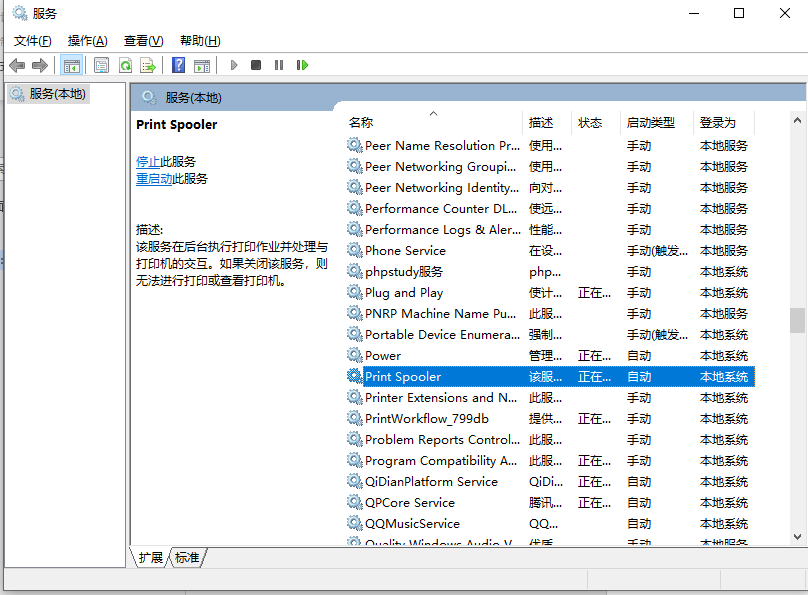
右键打开服务属性,将服务类型修改为“禁用”,并停止该服务。